*************HYDRA********************
My blog is close to me because I don’t look at it. Today are planning to go to sctf to solve some web challenges but not solve any questions. So,I went out with some challenges misc. They are on a simple level. Ok, come to challenge Hydra!!!
I give a compress file . When i extract it, i give a png with file name is hydra.png
As usual i try with the strings,exiftool,… command . But nothing except for some evidence like words Looking for flag…

Okay, i will binwalk it and i see , fuk*** w*w sh*i a lot of file embed it.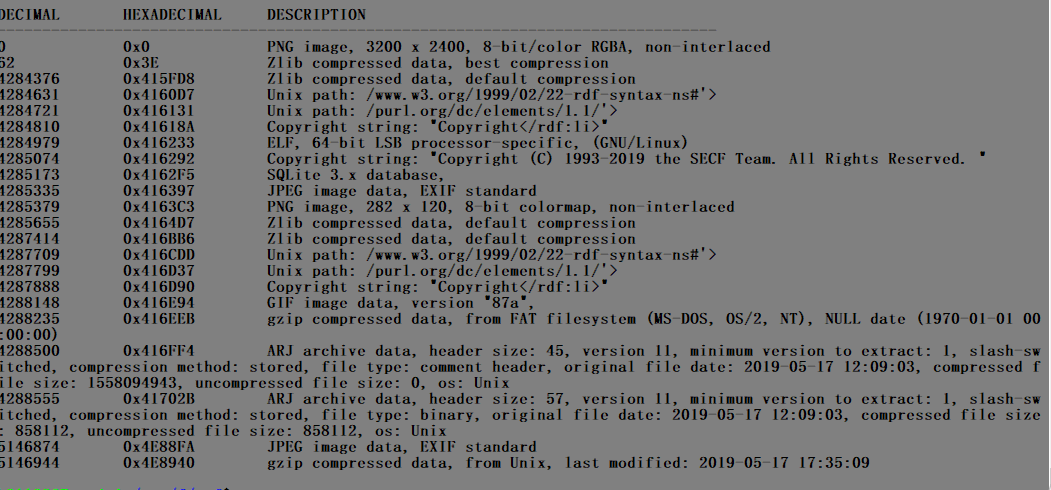
There are some interesting things here, there are some other pictures in it, I try to extract images with short code to see what it has ???
vl=open(“hydra.png”,”rb”).read()
xx = s[4285379:4287888]
open(“out.png”,”wb”).write(xx)
wow,This is a file png =.=
Continue, I try the exiftool command !
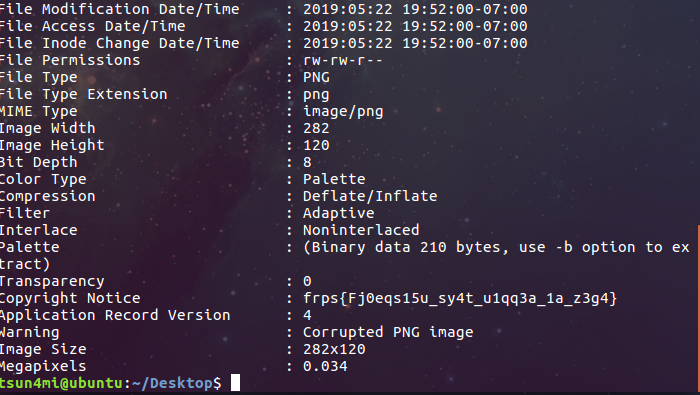
Yeah, flag here : frps{Fj0eqs15u_sy4t_u1qq3a_1a_z3g4}
But it is cipher text, i decode cipher text with key=12 to get flag real : sctf{Sw0rdf15h_fl4g_h1dd3n_1n_m3t4}
**************SIGNAL***********
Give pdf file from Server, i open it and see :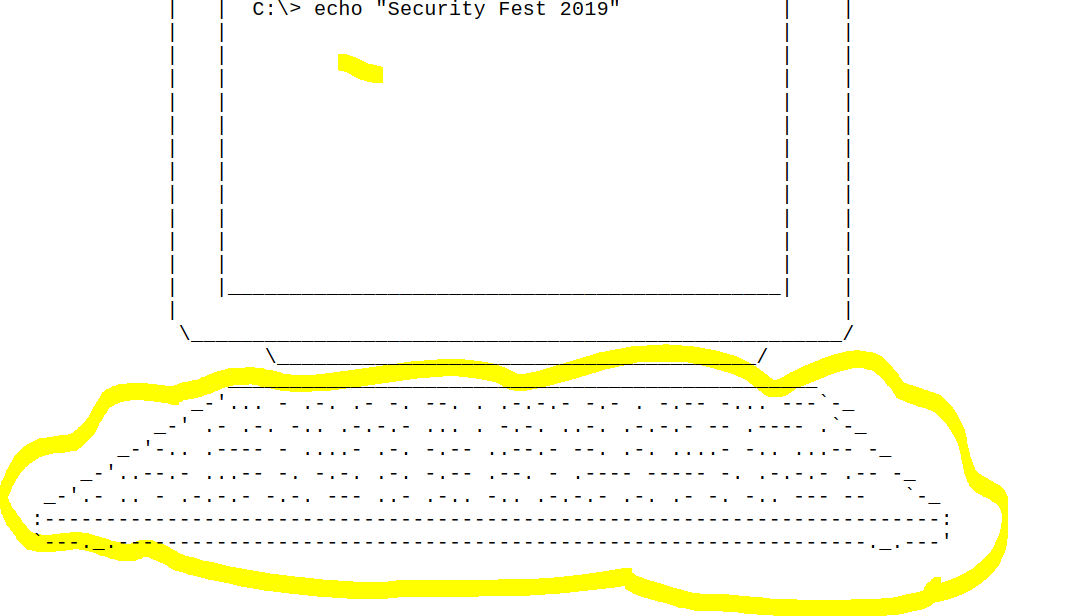
Easy to solve, This is the morse code, You decode it to get flag : xxxxxxxxxxxxxx Try hard (y)
Thank for readinggggggggg. ❤


“But it is cipher text, i decode cipher text with key=12 to get flag real”
Why the key=12
LikeLike
sorry, I code my own decode program and it starts counting from 0, instead, the online programs count from 1 . So, with my code . Key is 12 and Online decode key will be 13 …
LikeLike